Deceptive Website Targets Windows and Android Users
In a recent cyberattack, a group of hackers linked to Pakistan, known as APT36, has been found spreading malware through a fake India Post website. This malicious campaign aims to compromise both Windows and Android users by tricking them into downloading harmful files.
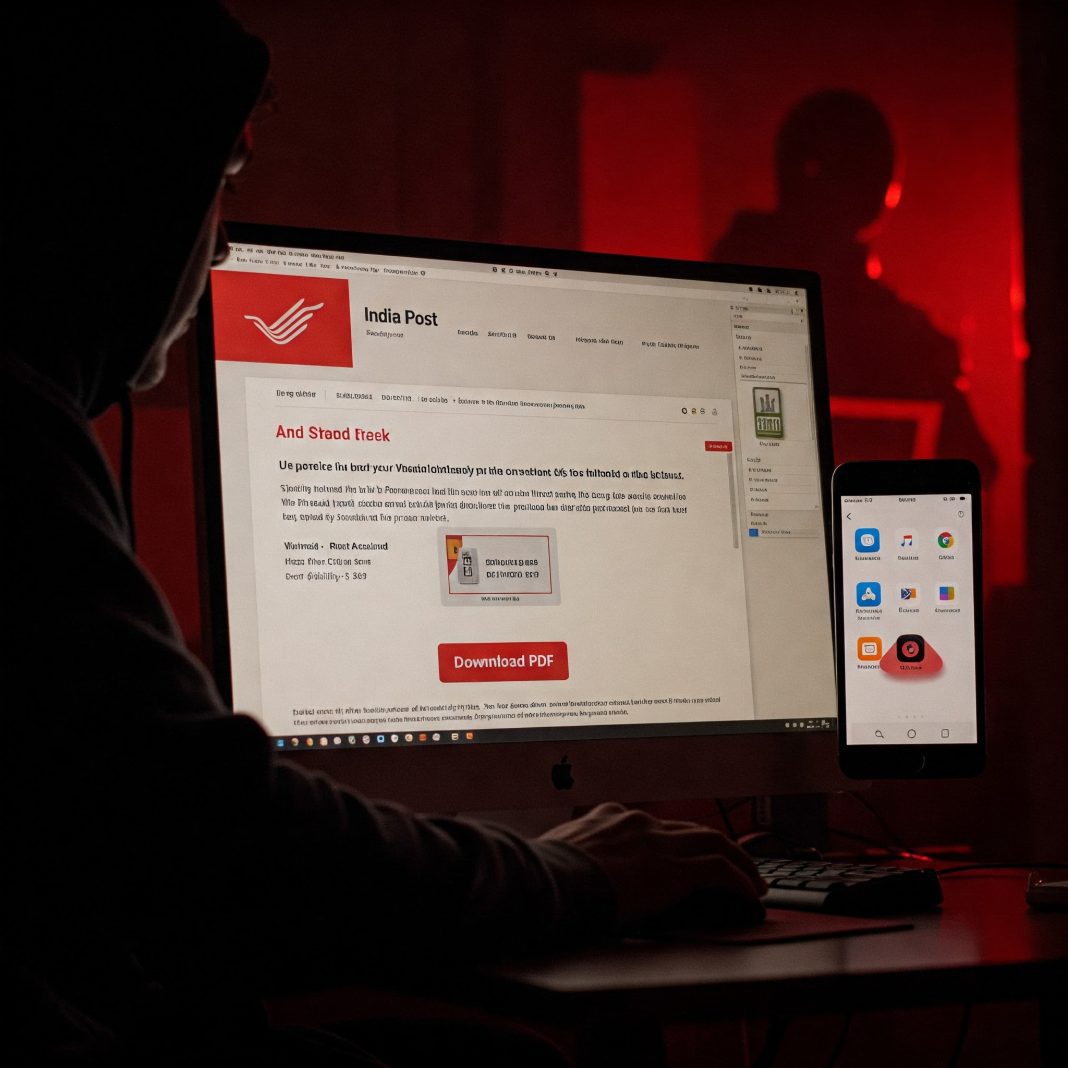
The fraudulent website, named “postindia[.]site”, is designed to look like the official India Post website. People who visit the fake site from a Windows computer are prompted to download what appears to be a PDF file. However, this file contains hidden instructions that can potentially give hackers access to the user’s system.
Android users, on the other hand, are directed to download an app called “indiapost.apk”, claiming it will offer a better experience. Unfortunately, the app is a dangerous tool designed to steal sensitive data from the user’s device.
How the Malware Works
When Windows users open the fake PDF, they see a document with “ClickFix” tricks. It tells them to press Win + R and enter a PowerShell command in the Run box. PowerShell is a tool that runs scripts and automates tasks on Windows. In this case, the command secretly downloads harmful files from a remote server. This lets the hackers take control of the system or steal important data.
Cybersecurity experts from CYFIRMA studied the hidden details of the PDF. They found it was created on October 23, 2024, by an author named “PMYLS.” This name likely refers to Pakistan’s Prime Minister Youth Laptop Scheme, linking it to Pakistani state-backed hackers. The fake website domain was registered a month later, on November 20, 2024. This gave the hackers time to plan and launch the attack.
Android users are lured into installing the malicious “indiapost.apk” app, which asks for extensive permissions. Once installed, the app secretly accesses and exfiltrates sensitive information, including contact lists, current location, files from external storage.
To avoid raising suspicion, the app disguises itself by changing its icon to look like Google Accounts, making it hard for users to recognize and delete. Even if the device is restarted, the app continues running in the background, collecting data and sending it to the hackers.
Worse still, the app is programmed to ignore battery optimization settings, ensuring it stays active at all times. If users deny any permissions, the app repeatedly asks for them until they are granted, making it extremely difficult to control.
Cyberattack Catastrophe: How Hackers Can Endanger Human Lives ?
Widespread Threat Using Deceptive Tactics
The APT36 group is not new to cyberattacks. They are known for using smart tricks to target government offices, businesses, and people, mainly in India. This latest attack shows they are getting smarter. They are now aiming at both computers and mobile devices at the same time.
CYFIRMA warned that the ClickFix trick is becoming more common. Hackers use it to fool people, even those who know about technology. It tricks users into running harmful commands. This helps attackers sneak into their systems without them knowing.
Cybersecurity experts stress that these types of attacks are extremely dangerous because they use realistic-looking websites and trusted names, like India Post, to fool users. By the time users realize they’ve been duped, their personal data may already be in the hands of cybercriminals.
How Cyber Attacks on Industrial Control Systems Can Endanger Lives ?