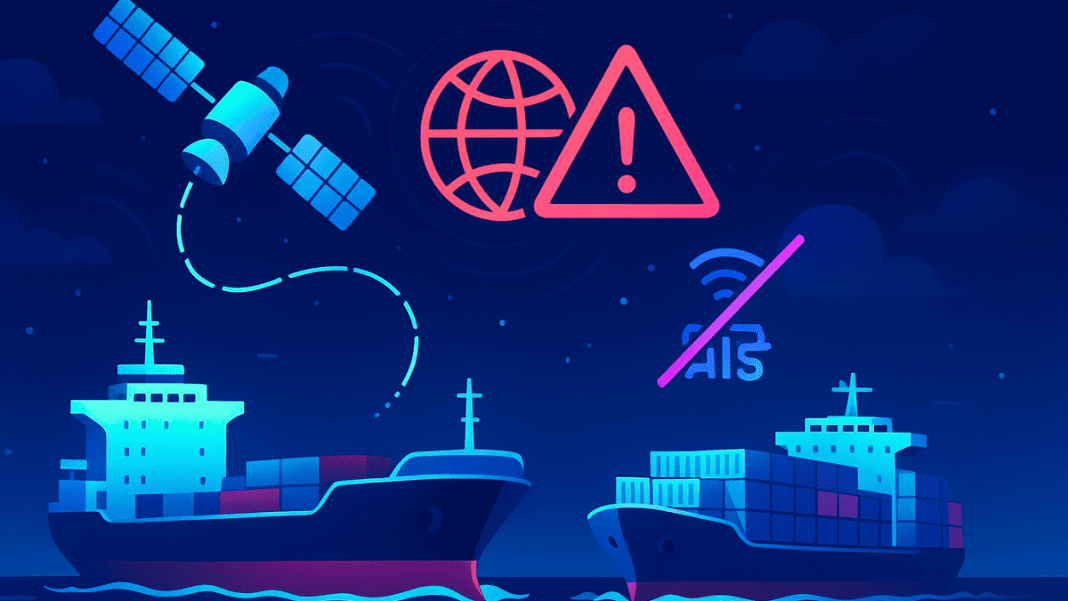
A major cyberattack has disrupted the communications of dozens of Iranian merchant vessels. A hacker group calling itself Lab-Dookhtegan has claimed responsibility for the operation.
Hackers hit Iran’s shipping networks
Reports say the attack disabled ship-to-shore communication systems of 39 oil tankers and 25 cargo ships operated by the National Iranian Tanker Company (NITC) and the Islamic Republic of Iran Shipping Lines (IRISL).
So far, NITC and IRISL have not confirmed problems. Cyber experts studied the claims and found them credible. They believe the hackers targeted ship communication networks.
This caused a large disruption in the systems.
Lab-Dookhtegan has launched similar attacks before. In March, it claimed to disable communications on over 100 ships. These ships were linked to the same two Iranian companies. That attack happened during military operations in Yemen. Observers see the group as part of a wider campaign. The campaign seems to target Iranian shipping activities.
How the hackers broke into systems
The hackers targeted Fanava Group, a private IT firm in Tehran. Fanava provides internet and satellite services for ships. It also runs networks used by merchant vessels.
The company operates a cybersecurity system called Falcon. Hackers claim they broke into this system.
The hackers broke into these systems. They blocked ship-to-shore communications.
They also disrupted AIS tracking. AIS helps ships share their location and movements.
Ports and coastal authorities use this information. Without AIS, it is harder to track ships.
This creates serious risks for safe navigation.
How Cyber Attacks on Industrial Control Systems Can Endanger Lives ?
Although little is known about Lab-Dookhtegan itself, the group seems to focus on Iranian targets. Cybersecurity experts have examined the techniques used in this latest attack and judged them as credible. An Israeli maritime cybersecurity company has stated that the tactics matched known cyber warfare methods.
Fanava, the company targeted in the attack, runs satellite networks and even financial services in Iran. Despite its central role in these sectors, the company does not currently appear on sanctions lists maintained by the US, UK, or EU. This makes the targeting of its systems particularly sensitive, as it highlights how companies not directly under sanctions can still be drawn into the conflict surrounding Iranian oil and shipping.
Growing pressure on Iran’s shipping activities
Iran’s shipping sector has long been under scrutiny because of international sanctions related to oil exports. In recent months, both the United States and the United Kingdom have expanded their enforcement to include not just ships, but also service providers linked to Iranian oil trade.
While US authorities have been aggressive in issuing fines and penalties for sanctions breaches, the UK has faced criticism for weak enforcement. Reports note that US regulators imposed hundreds of millions of dollars in fines this year alone, while UK authorities have taken only a few actions, none of them linked to Iranian oil.
Insider revenge cyberattack freezes 1,000 workers — Eaton hit with massive disruption and losses
Enforcement is a major challenge because of the complex networks Iran’s shipping activities rely on. These networks often use front companies, hidden ownership, and offshore service providers to avoid detection.
The latest hacking incident shows how Iran’s shipping operations remain exposed to both sanctions enforcement and cyber operations.