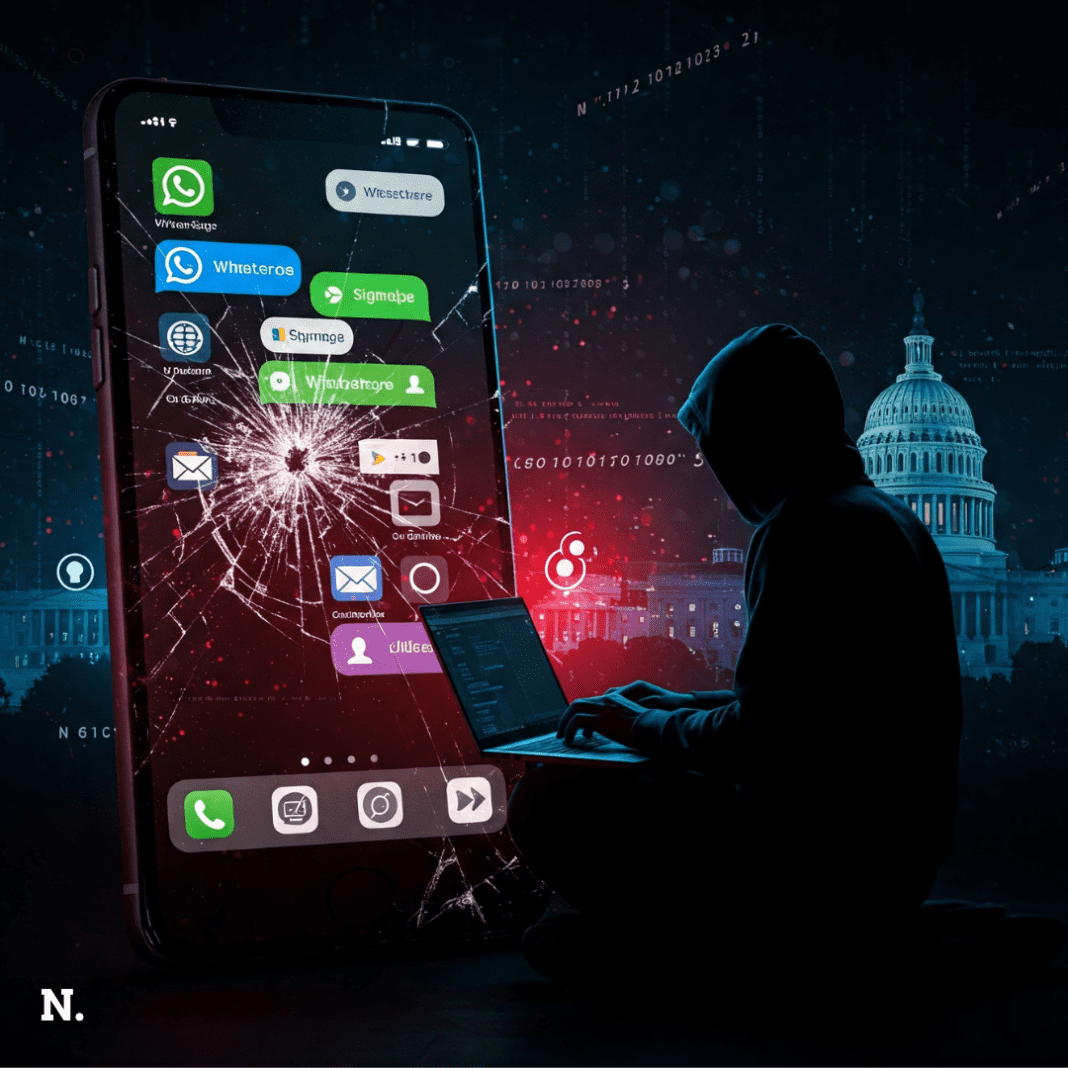
Private Contact Information Easily Accessible
The private contact details of top U.S. security officials were found online. This includes phone numbers, email addresses, and even some passwords. Investigative journalists uncovered the leak. They used people-finder services and hacked databases to get the data.
These services are usually used for marketing and hiring. However, they made it surprisingly easy to find sensitive information. By searching LinkedIn or running simple queries, reporters found the personal phone numbers and emails of top officials.
Even worse, messaging apps like WhatsApp and Signal linked to some phone numbers. People use these apps for private and sensitive chats. This means strangers could see their profile pictures, send messages, or even try to hack their accounts.
Leaked Passwords Pose a Major Risk
Along with contact details, the leaked data included passwords. The officials’ email addresses were linked to these. Hackers found the passwords in databases of stolen or hacked accounts. These databases are easy to find on the dark web and some forums.
Reporters linked some leaked passwords to the officials’ recent online activity. This means some passwords might still be in use. Hackers could use them to access private emails, log into chat apps, or enter online storage accounts.
The leaked email addresses were used to create accounts on popular apps. These include Microsoft Teams, Dropbox, and fitness apps. This gives hackers more ways to access the officials’ online accounts.
Experts say these leaks help criminals and spies to send fake but real-looking emails or messages. This could trick officials into sharing secret information or clicking dangerous links.
Critical Vulnerabilities: The Dark Side of Pacemaker Technology
Grave National Security Concerns
The leak of the officials’ private data is a big security risk. Some leaked numbers were linked to Signal and WhatsApp. This raises concerns that officials may have used personal phones for work chats.
The report says U.S. officials used Signal to talk about a military strike. They shared secret intelligence and attack plans. If the leaked numbers were in the group, enemies could have seen the chat.
Cybersecurity specialists have pointed out that having the personal phone numbers of high-ranking security officials makes it easier for hackers to install spyware on their devices. With spyware, attackers could eavesdrop on calls, read messages, and track locations.
The leak could lead to deepfake attacks. Criminals can use public photos and audio to make fake videos or voices. They could pretend to be the officials. This could spread false news or trick leaders in online meetings.
Even though the leak is serious, the government has stayed silent. Reporters tried to contact the Defense Department and the National Security Council. They also reached out to the officials’ offices. But no one has responded or made a public statement.
In a worrying sign, reporters sent messages to some officials on WhatsApp and Signal. The messages were delivered, showing the numbers are still active. However, no one has replied.
This huge data leak shows a big weakness in handling personal information. Even top security officials are at risk. The fact that their private details are easy to find online is alarming. It shows the need for stronger data protection, especially for government leaders.